الاستيراد (منخفض → مرتفع)
- يمنع البرمجيات الخبيثة من الدخول إلى الشبكات السرية.
- يجمع بين Multiscanning والتحليل Adaptive Sandbox والتحليل Adaptive Deep CDR والتحكم أحادي الاتجاه وفواصل البروتوكول.
تمكين التعاون الضروري للمهام الحيوية باستخدام حلول OPSWATالمعيارية والمصممة خصيصًا لهذا الغرض.
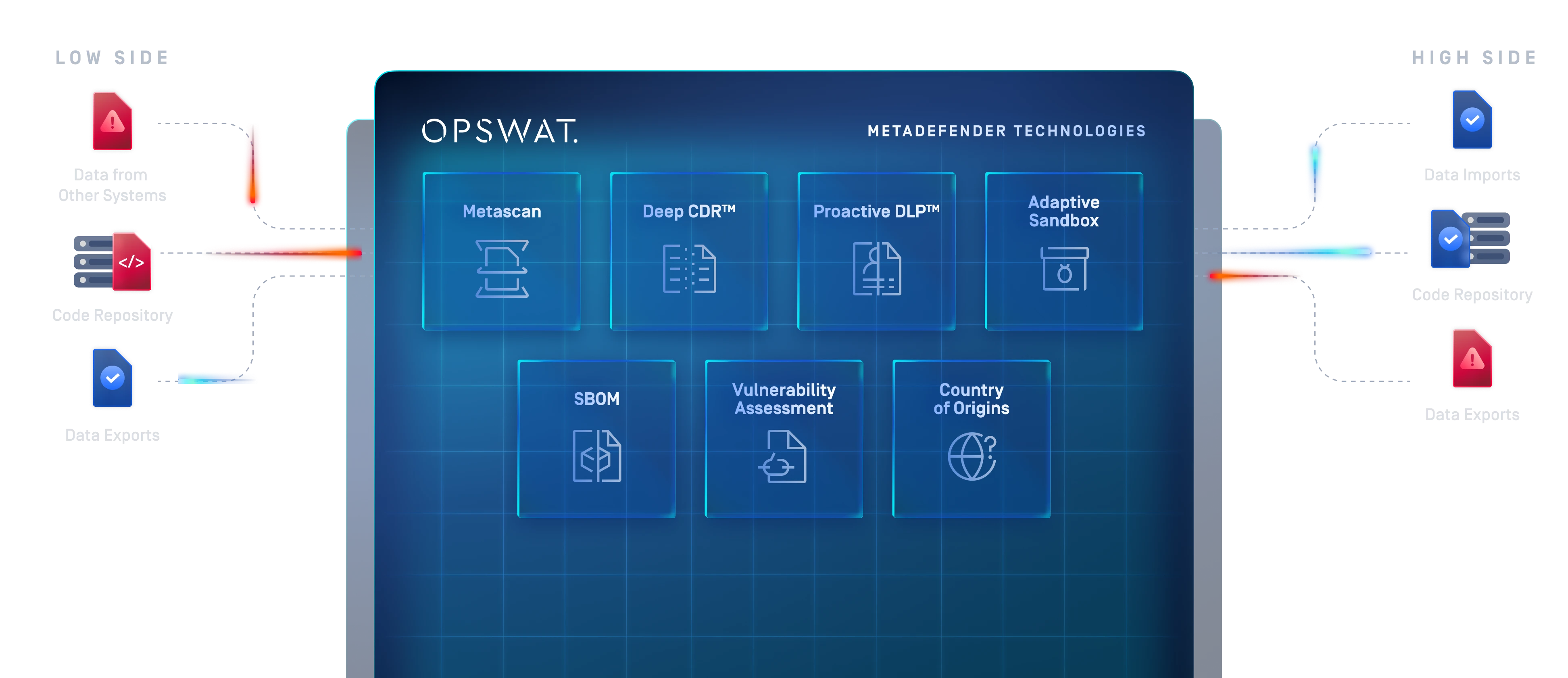


تأتي البيانات التي تنتقل عبر النطاقات الآن بأحجام كبيرة وتنسيقات متنوعة، من ملفات المستخدم اليومية إلى البيانات الجغرافية المكانية والمثبتات وتحديثات التطبيقات. تكافح الأنظمة القديمة والأنظمة التي تعتمد على الأجهزة فقط لمعالجة هذا التنوع ولا يمكنها التوسع لتقديم وظائف إنفاذ الأمن (SEFs) المطلوبة بطريقة مرنة وقابلة للتوسيع.


يجب أن تصمد الأنظمة أمام المهاجمين ذوي الحيلة العالية، بما في ذلك تهديدات الدول القومية. تكشف عمليات نقل البيانات بين مستويات الأمان عن نقاط الضعف التي لا تستطيع الدفاعات التقليدية معالجتها، بينما تتطلب الهجمات التي تعتمد على الذكاء الاصطناعي حماية حديثة وقابلة للتكيف.


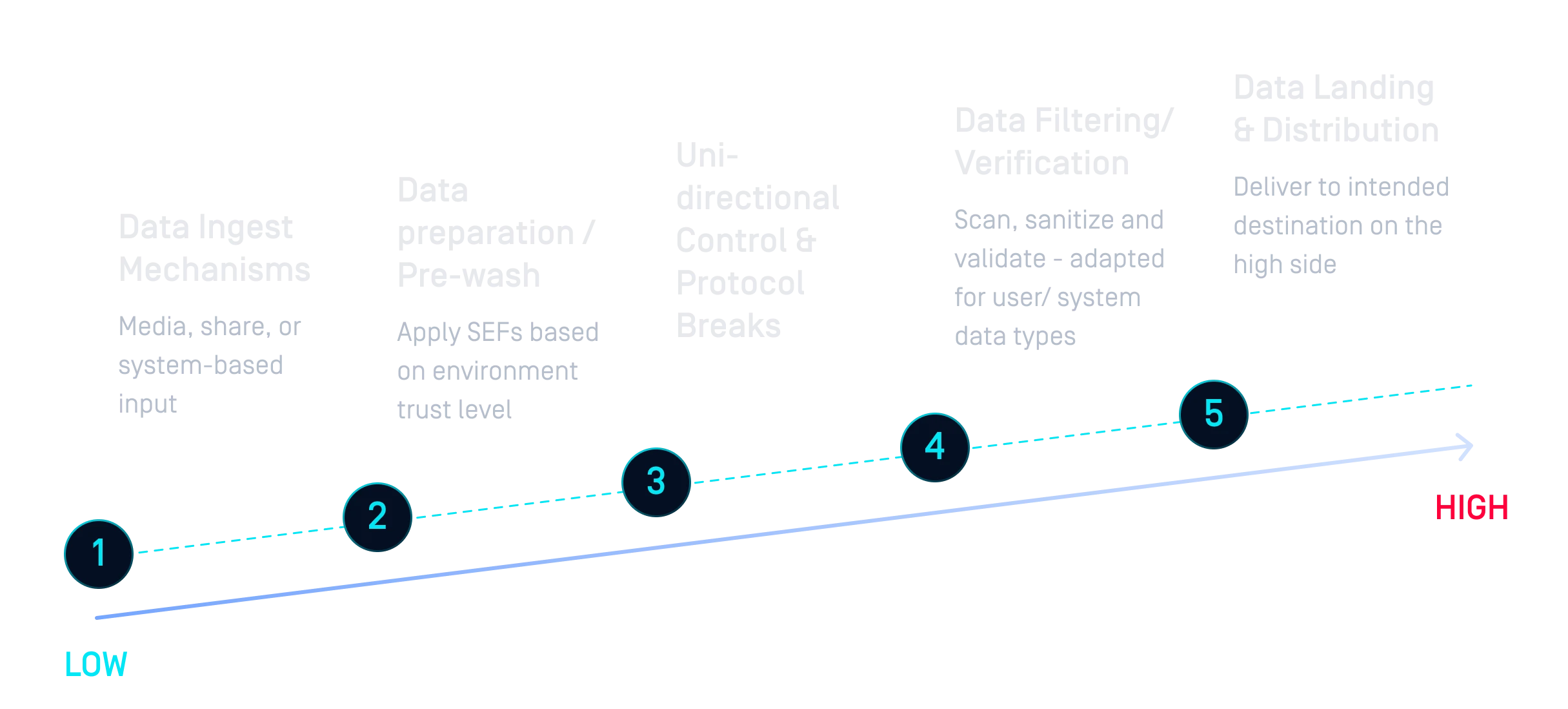
لم يعد عزل البيانات بشكل دائم يلبي احتياجات التعاون عبر الأقاليم. يجب أن تتكيف أنظمة CDS الحديثة مع متطلبات الأعمال، وتدعم أحجاماً وأنواع بيانات وتطبيقات متنوعة، مع تمكين عمليات نقل سلسة APIAPI API ومن السحابة إلى السحابة.
توفر OPSWAT نهجًا معياريًا قائمًا على البرمجيات التي تضيف إلى العمليات الحالية،
مع التقنيات الرائدة في السوق.
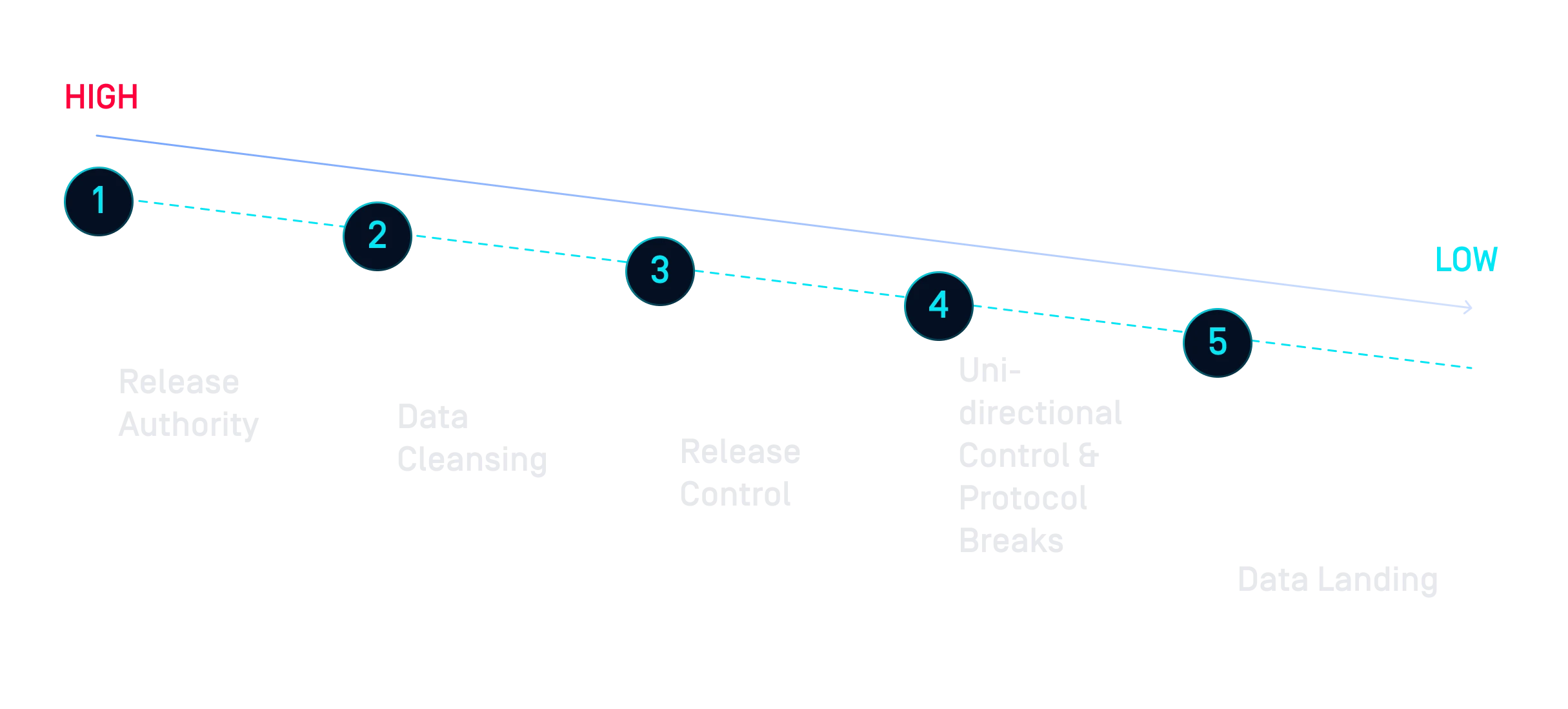
بفضل التقنيات الرائدة في السوق وإمكانيات التوصيل/الفصل، يُعد النهج المعياري OPSWATطريقة أكثر كفاءة لبناء حلول CDS.
باستخدام صندوق الحماية للمحاكاة، يمكن للمؤسسات النظر إلى مراكز العمليات التشغيلية الدولية في أنواع البيانات المعقدة مثل تصحيحات نظام التشغيل أو التطبيقات وإزالة ناقلات التهديدات المحتملة.
يمكن أن تساعد Proactive DLP في ضمان عدم احتواء البيانات المنقولة من تصنيفات أعلى إلى تصنيفات أدنى (مثل التقارير التي تتم مشاركتها مع الشركاء) على معلومات حساسة غير مخصصة للنشر، وذلك من خلال اكتشافها وحظرها داخل الملفات.
معKiosk MetaDefender Kiosk يمكن للبيانات القادمة من Media القابلة للإزالة أن تمر عبر آليات إنفاذ الأمان المناسبة بناءً على وضع المخاطر في مؤسستك.
إحدى المزايا الرئيسية هي أن استخدام MD Core أدوات MFT تتبع كامل للمراجعة، مما يمكّن المؤسسات من تتبع ومعرفة الدور أو الشخصية التي حاولت سرقة البيانات.
على عكس الأساليب التقليدية التي تعزل البيانات وتجعل التعاون صعباً، حلول OPSWATمع البنى المتعددة المجالات وتطبق سياسات الأمان. يدعم النهج الهجين للأجهزة والبرمجيات مجتمعات متعددة ذات اهتمامات مشتركة، مع ضمان التحكم في البيانات الحساسة ومراقبتها وتدقيقها بشكل صحيح.
مع ازدياد تطور الهجمات الإلكترونية والتهديدات التي تنفذها الجهات الفاعلة التي تقوم بها، تقوم الهيئات الحاكمة في جميع أنحاء العالم بتطبيق لوائح تنظيمية لضمان قيام البنية التحتية الحيوية بما يلزم للحفاظ على أمنها.